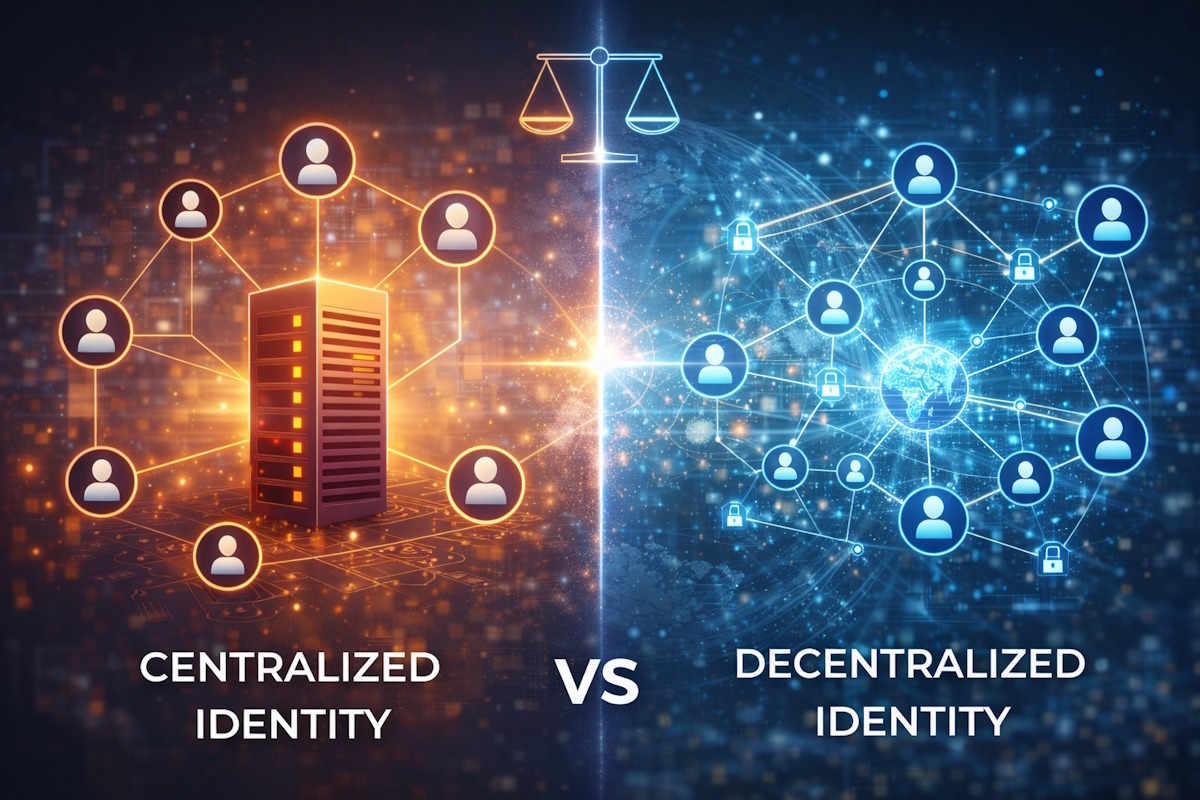
Behind every digital interaction lies an identity system that determines who is trusted, who has access, and under what conditions. Most digital services today rely on centralized identity models, yet alternative approaches are increasingly gaining attention. Understanding the differences between centralized and decentralized identity is essential for evaluating how trust, control, and risk are structured in modern digital systems
Digital identity systems define how individuals and organizations are recognized and trusted in digital environments. Over time, two fundamentally different models have emerged: centralized identity and decentralized identity. Understanding the differences between these models is essential for grasping the challenges of today’s digital systems and the motivations behind newer approaches such as Self-Sovereign Identity. Although both models aim to solve the problem of digital trust, they do so in radically different ways, with important consequences for security, privacy, control, and scalability.
Centralized identity is the dominant model used on the internet today. In this approach, a single organization or authority is responsible for issuing, storing, and managing identity data. Users create accounts on platforms or services, and their personal information is stored in centralized databases controlled by the provider. Authentication typically relies on credentials such as usernames, passwords, or biometric data, which are verified against these central repositories. Governments, social media platforms, banks, and large technology companies all operate centralized identity systems, often at massive scale.
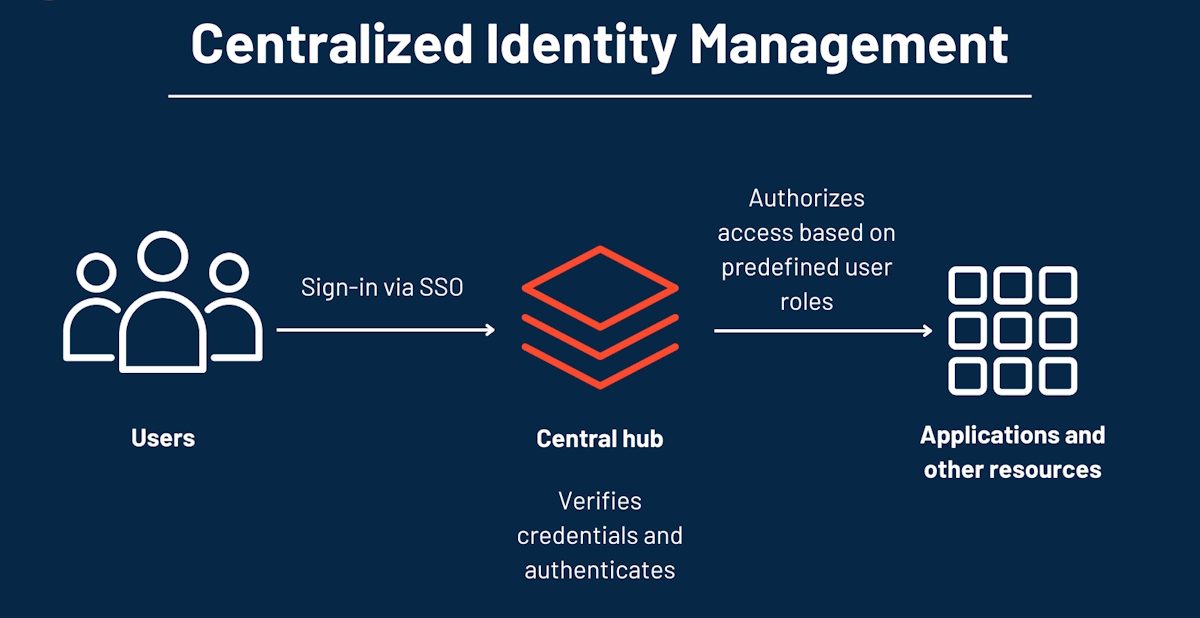
This model offers certain advantages. Centralized systems are relatively easy to deploy, manage, and integrate within closed ecosystems. They allow organizations to enforce consistent policies, monitor activity, and quickly update or revoke access when necessary. For many years, this approach enabled the rapid growth of online services and digital platforms. However, these benefits come at a significant cost. Centralized identity systems create single points of failure, where a breach, outage, or abuse of power can affect millions of users simultaneously.
A practical example illustrates these risks. When a user logs into multiple services using the same email address and password, those credentials are often stored in multiple centralized databases. If one of those databases is compromised, attackers may gain access not only to that service but also to others. Even when users follow good security practices, they have little control over how securely their data is stored or how it is shared internally or with third parties. The concentration of identity data also makes centralized providers attractive targets for cybercriminals, leading to large-scale data breaches with long-lasting consequences.
Beyond security concerns, centralized identity systems create structural power imbalances. The organization controlling the identity infrastructure effectively controls access to services, platforms, and digital participation. Accounts can be suspended, limited, or terminated, sometimes without transparent explanation or effective recourse. Users are typically required to accept extensive terms of service, granting providers broad rights over their data. As a result, identity becomes less a personal attribute and more a permission granted by an institution.
Decentralized identity proposes a different model. Instead of relying on a single central authority, identity data is distributed across a network, and individuals play an active role in managing their own identity credentials. In decentralized systems, identity is not stored in one central database. Instead, it is composed of verifiable credentials issued by trusted entities and held directly by the user, often in a secure digital wallet. Verification does not depend on querying a central repository, but on cryptographic proofs that confirm authenticity.
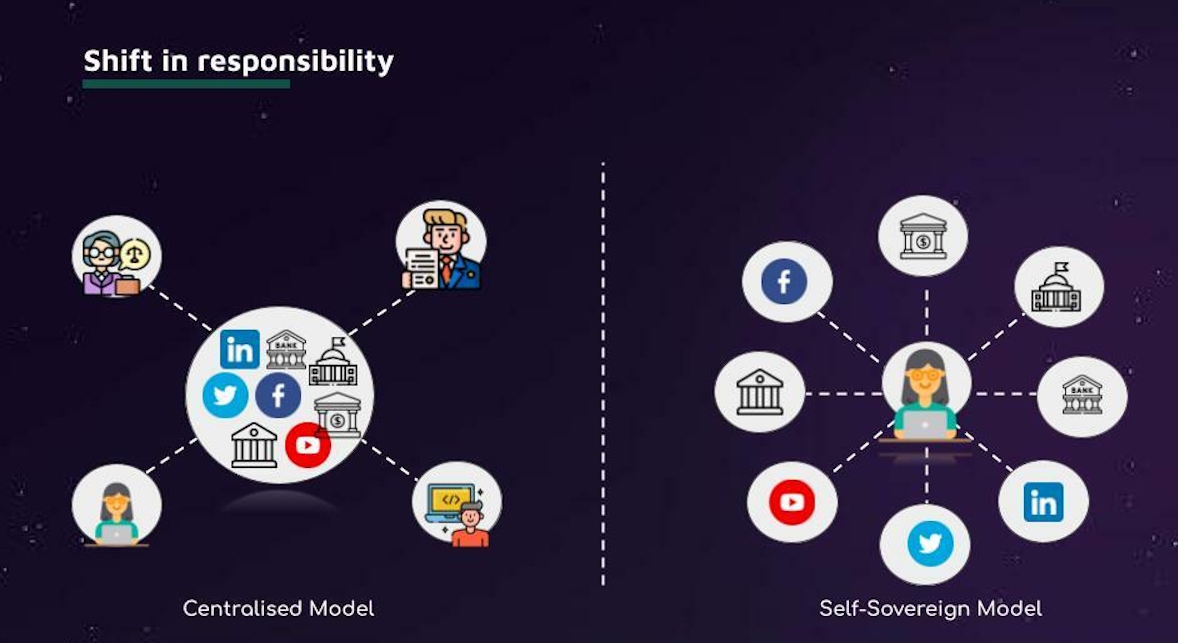
In this model, institutions still play an important role, but their role changes. A university, for example, can issue a credential certifying that a person has earned a degree. The individual stores this credential and can present it to employers or other institutions when needed. The verifier can check that the credential is valid and was issued by a trusted university, without contacting the university directly or accessing a central database of graduates. Control over when and how the credential is used remains with the individual.
The decentralized approach reduces many of the risks associated with centralization. Because data is not concentrated in a single location, large-scale breaches become more difficult. Users no longer need to repeatedly submit personal information to multiple providers, reducing data duplication and exposure. Decentralization also improves interoperability, as credentials issued in one context can be reused in others, provided common standards are followed.
A simple comparison helps clarify the difference. In a centralized identity system, accessing an online service typically requires creating a new account, submitting personal data, and trusting the provider to store and protect that data indefinitely. In a decentralized identity system, accessing the same service could involve presenting a verifiable credential that proves a specific attribute, such as eligibility or qualification, without creating a permanent account or handing over unnecessary information. The service verifies the proof, not the person’s entire identity profile.
Despite its advantages, decentralized identity also presents challenges. It requires new technical infrastructure, changes in governance models, and greater user responsibility for managing credentials and keys. User experience, recovery mechanisms, and institutional adoption are critical factors that must be addressed for decentralized systems to function at scale. Decentralization does not eliminate trust, but redistributes it across multiple actors and technical guarantees.
In summary, centralized and decentralized identity models represent two distinct ways of organizing trust in digital environments. Centralized identity prioritizes control, efficiency, and institutional authority, but concentrates risk and power. Decentralized identity emphasizes user control, resilience, and interoperability, but requires new approaches to design, governance, and adoption. Understanding this distinction is key to evaluating the future of digital identity and the broader shift toward more user-centric and trust-preserving digital systems.