In the rapidly evolving digital landscape, the concept of identity is undergoing a profound transformation. As Web3 technologies challenge the centralized models of the past, a new paradigm is emerging—one where individuals can own and control their digital identities without reliance on intermediaries

Decentralized identity within the Web3 ecosystem represents not merely a feature of emerging digital infrastructures but rather a foundational component essential to the reconfiguration of trust, access control, and credential verification on the internet. As the evolution of Web3 progresses beyond its initial stages of speculative token markets and isolated decentralized finance (DeFi) protocols, identity management emerges as the critical layer that underpins user sovereignty, platform interoperability, and the preservation of privacy in digital interactions. In the absence of robust decentralized identity frameworks, there is a substantive risk that Web3 will replicate the structural dependencies and vulnerabilities of Web2 systems, albeit under a new technical architecture. The promise of a user-centric, censorship-resistant, and interoperable web cannot be fully realized unless identity itself is reengineered to reflect these values at the protocol level.
In its most fundamental form, decentralized identity in the context of Web3 refers to systems in which individuals independently generate, manage, and utilize their digital identities without reliance on centralized authorities such as social media platforms, corporate directories, or government-issued databases. The primary shift in this paradigm is the transition from identity issuance being controlled by institutions to identity being derived cryptographically from user-held private keys. Instead of logging into a digital platform through third-party identity providers, individuals in Web3 authenticate themselves through cryptographic signatures generated by their wallets. This transformation reframes identity as a function of key ownership rather than institutional permission, thus decoupling authentication from central control and aligning it with the broader ethos of decentralization and user sovereignty.
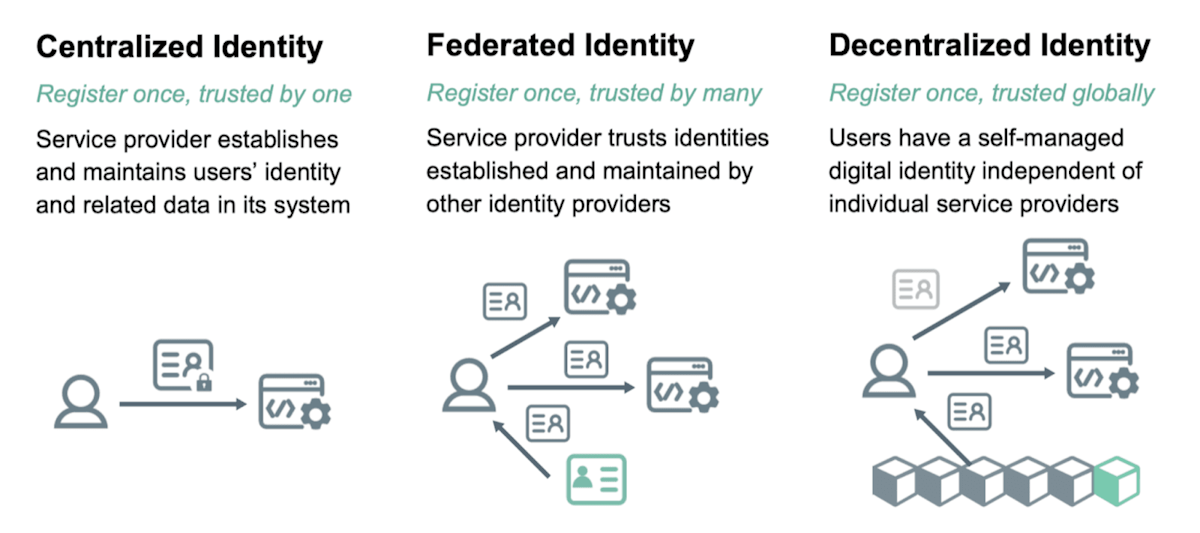
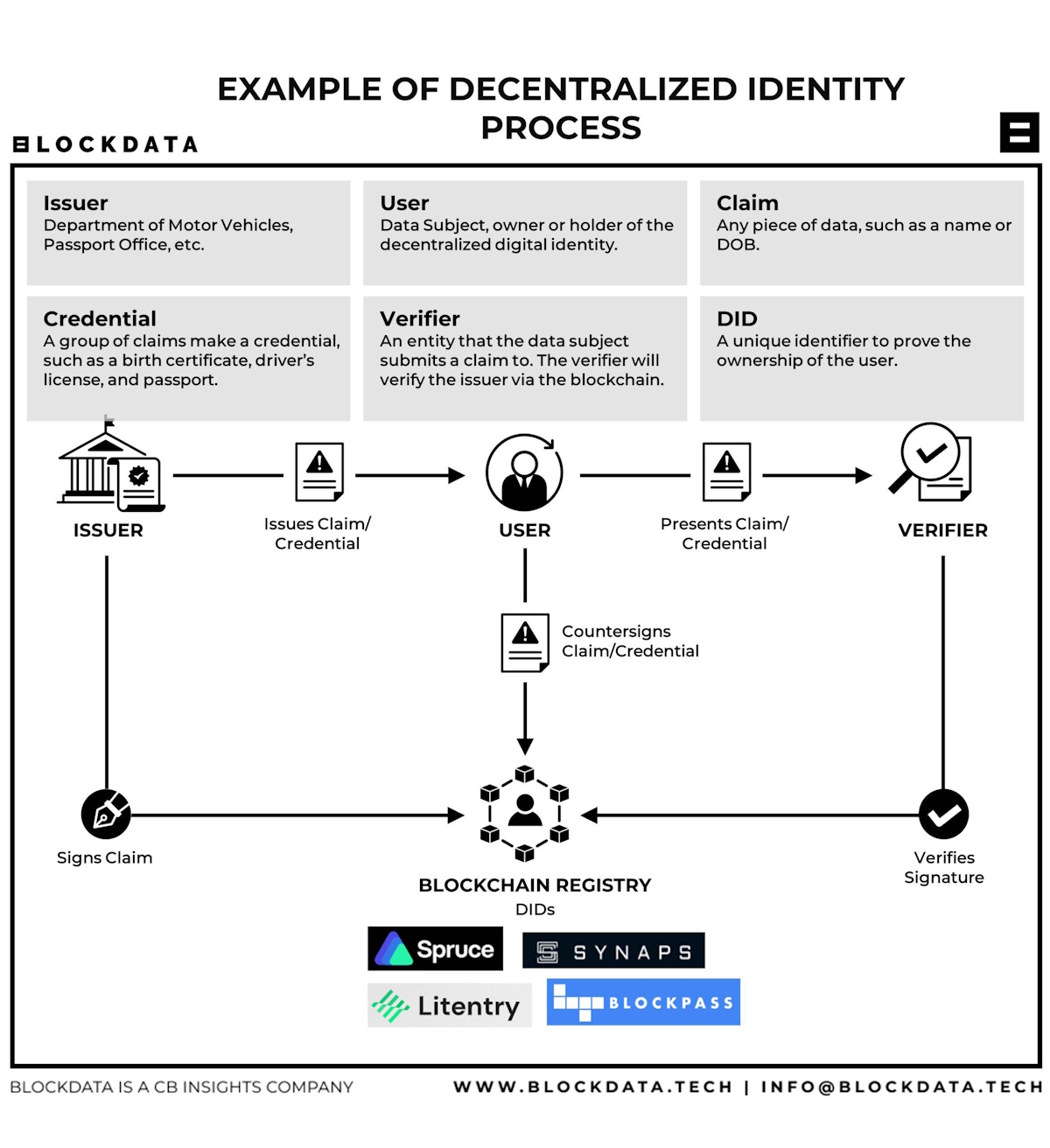
Within the blockchain domain, decentralized identity is operationalized through the integration of distributed ledger technologies as trust anchors, rather than as repositories of personal data. Crucially, blockchains do not store raw identity data such as names, addresses, or biometric information. Instead, they maintain references to decentralized identifiers (DIDs), public keys, and cryptographic proofs, which can be used to establish verifiable claims without revealing sensitive information. DIDs are globally unique identifiers that are generated and controlled by users, with no need for registration through centralized systems. They serve as resolvable pointers to public key infrastructure and associated metadata, enabling the establishment of trust between parties without requiring prior interaction.
Verifiable credentials (VCs) complement DIDs by allowing trusted entities such as educational institutions, healthcare providers, governments, and employers to issue attestations to users in a digitally signed and cryptographically secure manner. These credentials are stored by the users themselves, either locally or in encrypted decentralized storage, and can be selectively disclosed to third parties through the use of zero-knowledge proofs and other privacy-preserving techniques. The result is a system in which individuals can prove specific attributes about themselves, such as age, citizenship, or professional qualifications, without exposing the entirety of their identity profile or relying on centralized intermediaries for validation.
While Web3 aspires to eliminate the reliance on intermediaries, the reality is that many applications currently within the ecosystem continue to depend on centralized identity infrastructures. Users frequently interact with custodial wallets managed by third parties, undergo Know Your Customer (KYC) procedures through centralized vendors, or authenticate through platform-specific accounts. This reliance introduces critical points of failure, including data breaches, censorship vulnerabilities, and user lock-in, all of which undermine the decentralization narrative. An application that brands itself as decentralized but relies on centralized authentication mechanisms ultimately reproduces the power asymmetries and security liabilities characteristic of Web2.
Decentralized identity in Web3 offers a coherent solution to this contradiction by enabling identity to exist independently of any particular application, service, or platform. When identity is bound to cryptographic ownership rather than to institutional issuance, it becomes portable, composable, and persistent across the broader Web3 ecosystem. A user can maintain a single identity across multiple decentralized applications (dApps) without the need to re-register, re-authenticate through third parties, or obtain new permissions. This not only enhances user experience but also strengthens privacy, as the same credentials can be reused without repeatedly disclosing the underlying data to multiple service providers.
It is essential to recognize that Web3 is decentralized in its architectural design, but its operational reality is often less so. The use of smart contracts and distributed consensus mechanisms does reduce dependency on centralized entities to some extent, yet the layers that enable identity, governance, and onboarding remain heavily centralized in many deployments. Without decentralized identity, the claim of disintermediation within Web3 remains partial and, in many respects, superficial. Control over access rights, credential issuance, and reputation systems continues to reside disproportionately with platform developers and infrastructure providers. Thus, the degree of decentralization in Web3 must be assessed along a spectrum, and identity management plays a pivotal role in determining the system’s position on that spectrum.
It is also important to differentiate between the broader concept of Web3 and the more narrowly defined domain of decentralized finance. While DeFi is a significant subfield of Web3, primarily focused on peer-to-peer trading, lending, and asset management, Web3 encompasses a much wider range of functionalities including identity, governance, decentralized storage, social networking platforms, gaming ecosystems, and coordination tools. The principles of decentralized identity extend across all these domains. Within DeFi, identity enables credit scoring, compliance with regulatory requirements, and the formation of on-chain reputations, all without introducing centralized intermediaries. Outside the financial sphere, identity supports decentralized autonomous organization (DAO) governance, selective content moderation, access control to digital and physical spaces, and verified ownership of non-fungible tokens (NFTs) and other digital assets.
From a systems perspective, decentralized identity in Web3 adheres to a well-defined lifecycle. The process begins when a user creates a digital wallet that generates and controls a unique set of cryptographic keys. These keys form the basis of the user’s identity and are never shared publicly. The wallet establishes a decentralized identifier that is anchored on a blockchain to enable global resolution and verification. Trusted issuers can then issue verifiable credentials that are cryptographically linked to this identifier. The user maintains full custody of these credentials and may store them in encrypted personal storage or decentralized identity wallets. When required to verify a claim, the user can generate cryptographic proofs that validate the authenticity and integrity of their credentials without revealing the underlying personal information. This architecture fundamentally removes the need for centralized identity databases while maintaining a high standard of verifiability, auditability, and security.
Different projects on-going
Several real-world implementations illustrate how decentralized identity is being deployed at scale within the Web3 environment. Ethereum, as the most mature smart contract platform, enables wallet-based identity through the use of message signing and key-based authentication. A user can prove control over an Ethereum address by signing a message, thereby establishing a consistent identity across applications without any centralized issuance mechanism. Polygon, an Ethereum-compatible Layer 2 network, has supported identity systems focused on low-cost credentialing and scalability, including event attendance records, access passes, and experimental implementations of proof-of-personality protocols. These demonstrate how decentralized identity can be implemented efficiently and affordably, even in environments with high user throughput.
Worldcoin, a controversial project in the decentralized identity space, explores proof-of-personhood through the combination of biometric verification and blockchain-based identity issuance. Users are enrolled via biometric orbs that scan irises, creating a unique identifier that verifies human uniqueness without disclosing personal identity details. While the project has raised significant ethical and privacy concerns, it highlights the broader tension between technological feasibility and normative considerations in decentralized identity systems. Another initiative, developed by Spruce, introduces the “Sign-In with Ethereum” standard, which replaces traditional login systems with wallet-based authentication. This model eliminates the need for passwords, reduces exposure to phishing attacks, and aligns user authentication processes with the principles of cryptographic self-sovereignty.
The structural advantages of decentralized identity systems in Web3 are considerable. Users retain full ownership and control of their identity, eliminating the need to trust third parties with sensitive personal information. Platforms reduce legal and operational risk by avoiding the collection and storage of personally identifiable information. Privacy is significantly enhanced through selective disclosure mechanisms and zero-knowledge proofs, which ensure that users only share the minimum necessary data to prove specific claims. Security is also improved by minimizing centralized attack vectors and removing the reliance on static credentials that can be easily compromised.
Nonetheless, there are substantive challenges that remain unresolved in the development and deployment of decentralized identity systems. The complexity of the user experience continues to be a barrier to mainstream adoption, particularly for individuals unfamiliar with cryptographic key management. The irreversible nature of key loss introduces risks that are difficult to mitigate without reintroducing custodial elements, which may compromise decentralization. Standards for decentralized identity remain fragmented across various ecosystems, resulting in limited interoperability and hindering composability. Furthermore, legal recognition of self-sovereign identity is uneven across jurisdictions, with regulatory frameworks often lagging behind technological innovation.
In conclusion, decentralized identity is not an auxiliary component of the Web3 stack but rather a prerequisite for achieving its full potential. It serves as the mechanism by which individuals can reclaim control over their digital existence, establish trust in peer-to-peer environments, and interact across platforms without institutional mediation. The maturation of decentralized identity standards and their integration into core Web3 protocols will play a decisive role in shaping the future architecture of the internet and in determining whether it will fulfill its promise of decentralization, autonomy, and resilience.
